The edge-to-cloud continuum space covered by the ACCORDION platform, as any resource space, is potentially exposed to external threats and attacks. Thus, to clear out as much as possible the potential security glitches, ACCORDION evaluates, specifies and incrementally implements some tools and mechanisms to ensure the platform security and protection from breaches.
The ACCORDION platform is made up of a number of constituent components and is slated to host its client applications, providing them with proper resource allocation in the edge-to-cloud continuum, plus (in an incremental way) runtime quality of service and quality of experience active control. Security assurance encompasses both the ACCORDION component themselves and the application workload executing in the ACCORDION federated domain.
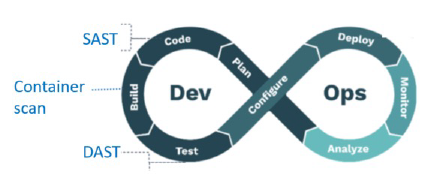
ACCORDION security checks include three kinds of verification:
- SAST (Static Application Security Testing); this check is performed on source code of software components, to ensure the code doesn’t include any intrinsic vulnerability
- DAST (Dynamic Application Security Testing); this check is performed on the application as black-box at runtime, to capture vulnerabilities not detectable in static mode
- Container security; this static check is applied to application module images before instantiating them, to capture vulnerabilities in the package or sparked by certain dependencies
The project performed an initial analysis of best-fitting tools to fulfil each of these security checks. In the first project implementation and validation cycle, the first of them (SAST) will be implemented, and the chosen tool for this is SonarQube [1]. SonarQube main advantage is its multiple language support, allowing to scan code written in a breed of different languages.
For the other phases, whose implementation will eventually be part of the next development cycles, candidate tools have also been scouted and some of them have been chosen as a candidate. For the DAST feature, based on typical penetration tests, OWASP Zap [2] is the potential candidate tool. More tools are in the shortlist for the container scanning function, including Anchore, Clair and Harbor.
[2] https://owasp.org/www-project-zap/
Author: Marco Di Girolamo | HPE